Quantum computers are set to become a reality. In addition to solving complex problems that we cannot solve in our current computing landscape, they’re also capable of breaking forms of encryption that are widely used today.
A survey collected the opinions of over 30 experts in the field, resulting in a Quantum Threat Timeline Report. According to this report, there’s a chance that in the next few years, it might take less than a day to break encryption with a quantum computer.
What needs to be done, though? What should leaders be doing now?
Defining public key cryptography and post-quantum cryptography
Before we get to that, let’s first define public key cryptography (PKC) and post-quantum cryptography (PQC).
PKC refers to most of the encryption that secures our digital interactions. Various quantum algorithms (such as Shor’s) have proven that PKC is vulnerable to quantum computers.
Post-quantum cryptography (PQC) refers to the encryption that both conventional and quantum computers will not be able to get past.
Why does my organization need to care?
If your response to the quantum threat is that you aren’t troubled by the thought of an “evil state actor with a quantum computer” getting access to your transaction data and quarterly sales reports from five years ago, that might seem reasonable.
However, just about all of society’s infrastructure — internet communications, e-commerce, healthcare, transport, energy, government and even national security — relies on well-functioning, reliable encryption. Here are three reasons why post-quantum cryptography matters.
Some PKC schemes are being deprecated
National Institute of Standards and Technology (NIST), the US agency that promotes standards and measurement, recommends deprecating some cryptographic schemes by 2030 and disallowing them by 2035. This means that PKC that uses these schemes to secure cloud, email, networks, applications, etc., will be flagged as insecure; it will no longer be trusted.
Whether a powerful enough quantum computer is available by then or not becomes slightly less relevant, given the depreciation of these standards.
Harvest now, decrypt later attacks
It’s possible that attackers are collecting encrypted data now and storing it to decrypt it with a quantum computer in the future. This means that if your organization has data that needs to be kept secret in the long-term, it’s at risk now. Examples of such data include medical records, intellectual property or personally identifiable data.
Migrating to PQC
NIST has developed a set of quantum-safe encryption schemes that will replace PKC. These standards have been put together as part of a long process that began in 2016 to evaluate various cryptographic schemes.
NIST’s new PQC standards
This is the list of NIST-approved schemes — some of which will be used to encrypt data and some to protect digital signatures. These algorithms have been proven to be quantum safe.
CRYSTALS - Kyber
CRYSTALS - Dilithium
Sphincs+
Falcon
HQC
Three steps to becoming quantum-secure
PQC migration is a two CEO problem, because it takes that long.
Organizations are now able to migrate their existing schemes to these NIST approved standards. This migration is a daunting task; there are huge costs involved and management support is essential. This is why Ben Packman of post-quantum organization PQShield calls PQC migration “a two CEO problem.” What makes it even more challenging are the legal unknowns and lack of any actual specific ‘Q-day’ timeline.
However, there are also costs to inaction. CIOs/CISOs and their teams who want to mitigate the risks of a post-quantum world can make use of this three-step plan to migrate to quantum-safe cryptographic schemes.
The PQC migration team need to:
1. Prepare a cryptographic inventory
This involves understanding and reviewing all cryptographic assets in use. This includes certificates, key management systems, protocols like TLS/SSL, libraries and hardware security modules. Essentially, all tools that enable secure storage and communications.
Teams should also assess and list all apps, systems, networks and data that rely on existing cryptographic assets. If there’s any sensitive data which needs to be kept secure for a significant length of time, that should take priority.
This can be a long process, but identifying highly sensitive data first can get the process started.
2. Assess the impact and cost of (not) moving to PQC
The next step is to explore whether the data and systems in the inventory are sufficiently secured. It’s often the case that security risk is also external, in your supply chain: cloud providers, SaaS providers and software vendors.
Then, consequences of a breach, like reputational damage and data loss needs to be addressed. This exercise will help gauge the organization's risk tolerance.
The team should then pick a timeline for PQC migration and work out the cost. The cost will ultimately consist of software tools and licences, hardware upgrade costs, human costs, testing, and downtime. A large part of the effort will be in aligning with third party migration roadmaps.
3. Build resilience
Simply moving to the NIST algorithms is not enough. It’s also important to consider the following:
Cryptoagility. This is the ability to upgrade or switch encryption quickly and adapt as necessary.
Catastrophic events. It’s essential to use layered defenses for data that’s in storage, in transit or in use; key management systems and monitoring can help here.
Recovery strategy. Having robust key management, backups, monitoring and incident response plans is vital.
Scaling resilience. It’s important to ensure the new encryption can be used across millions of devices and apps without degrading performance.
Mosca’s theorem
A good indicator of when to take action is summarized by the industry’s most well known quantum risk management principle formulated by Michele Mosca:
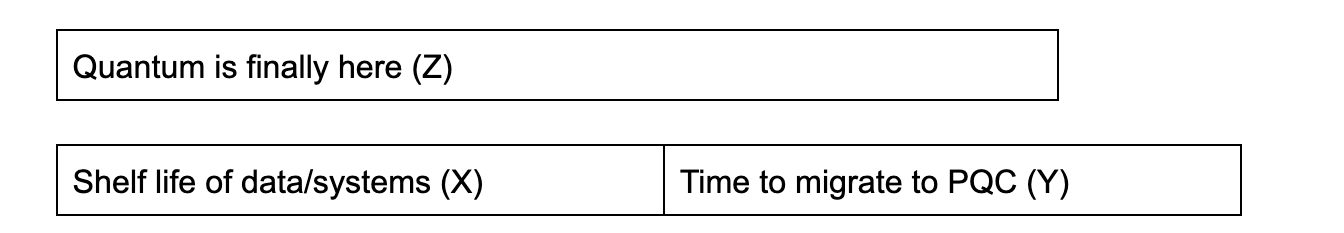

If X + Y approaches Z, it is time to act!
In other words, if the time that data needs to be kept secured and the time it takes to migrate to a quantum safe encryption, is close to the time that quantum computers might be available, act now! Following the three steps outlined and implementing a robust plan can help overcome the risks of a post-quantum world.
Disclaimer: The statements and opinions expressed in this article are those of the author(s) and do not necessarily reflect the positions of Thoughtworks.


















