Digital transformation is now the enterprise holy grail. An important part of this journey is cloud adoption as organizations leverage new technologies like containers, Kubernetes, serverless computing, machine learning, etc. During transformation projects, companies typically follow established industry practices around continuous delivery and DevOps but overlook one key aspect: security.
Cloud opens up a whole new world for cyber attackers to exploit data. Recently, McAfee found that post-pandemic, “threats from external actors targeting cloud services increased 630%, with the greatest concentration on collaboration services like Microsoft 365.” In fact, everyone from Alibaba to the Australian Parliament House has been breached.
One of the key reasons this happens is that organizations don’t realize that adopting the cloud will not absolve them of the responsibility of securing applications.
In a data center model, you are responsible for security across different operating environments such as your applications, physical servers, user controls and even the physical security of the building. Whereas in a cloud environment, your cloud vendor typically takes care of lower-level infrastructure, including related security. However, you are responsible for the rest.
This is called the shared responsibility model. In this article, we explore what the shared responsibility model entails and how you can protect your cloud services.
Cloud vendor-agnostic shared responsibility model
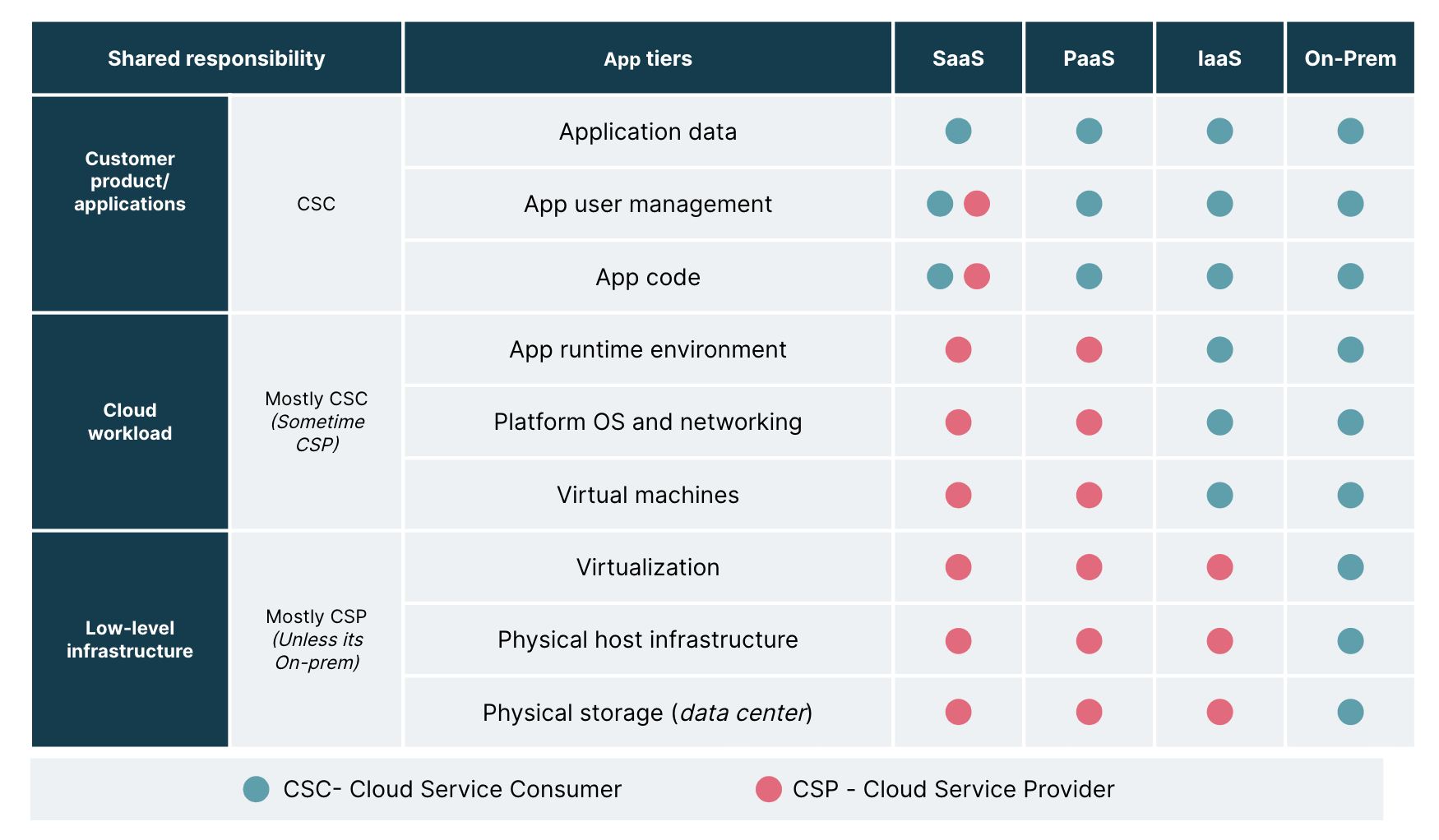
The cloud services or the workload responsibilities vary depending on whether the workload is hosted as software as a service (SaaS), platform as a service (PaaS), infrastructure as a service (IaaS) or on-premise. So, it is crucial to understand how each of these differs from the other.
Software as a service refers to products that are available as a service managed by a vendor on the cloud, such as Salesforce, Slack and Google apps
Platform as a service refers to products available as software tools and hardware infrastructure such as GitHub, Kubernetes and Docker
Infrastructure as a service refers to a set of infrastructure tools available as a ‘pay-as-you-go’ service such as Google compute engine, AWS, Digital Ocean, Red Hat
On-premise refers to products hosted from your in-house resources, like a data center within your firewall
Whatever the model, there is always some share of your responsibility for securing applications. For instance, in the PaaS model, low-level infrastructure like guest OS or networking controls are typically managed by the cloud provider, whereas application-related controls like code and user access management are managed by the customer. In the IaaS model, the host operating system, storage etc. are handled by the provider, while network security, container security and application controls are managed by you.

Reference: www.cloudsecurityalliance.org
As you can see in the diagram above, it's a control versus convenience dilemma. When we move from on-prem to IaaS, PaaS or SaaS etc., the cost of ownership decreases while your share of responsibility increases. Even though cloud providers offer features for security and compliance, they do not guarantee the protection of users, applications and service offerings.
What investments do business executives need to make?
Cloud security is more than just a technology issue. We believe that culture and processes play an important role in DevSecOps momentum, necessitating cross-functional coordination to build a talent pool, assess cyber threats/financial loss, and ensuring compliance. Here are three kinds of investments that leaders must make:
Understand your responsibility
Reports suggest that a majority of cloud security failures are the customers' fault. So, carefully understand your part of the shared responsibility as early as possible to relieve the operational burden and avoid potential data leak or cyber threats. Understand the boundaries of responsibility and build capabilities to address your share effectively.
Bring on the right talent
Bring on technology leaders who are passionate about cloud computing as well as security. Ensure that you have teams that can approach security from various angles, including application security, data security, compliance and the like. Build capabilities that evolve with the changing needs of the market, applications and customers.
Building security in
Embed security practices into your software development process to strengthen your products. Implement a secure path to the production pipeline. Shift left by integrating and testing for security with SAST (tools like Veracode), dependency scanners (Trivy), Secrets scanner (Talisman) and DAST (Burp Suite) early in the cycle.
Make sure the applications are not hosted on a flat network. Use proper information security principles like Defence in Depth to secure confidentiality, integrity, and network and data availability. Consider ‘Build Security In’ early rather than bolting it late in the development process.
The future technology landscape will be hybrid, diverse and multi-cloud. The need for cloud computing will evolve as organizations adapt to support scalable environments. To be secure in such a world, enterprises need to invest strategically in threat modeling, automating and orchestrating containers, configuring security controls between on-premise to cloud, and building a secure path to the production pipeline.
Disclaimer: The statements and opinions expressed in this article are those of the author(s) and do not necessarily reflect the positions of Thoughtworks.


















